Step-by-Step Guide: Setting up Environment Variables in GitHub Actions for Go
Introduction:
GitHub Actions is a powerful platform that allows developers to automate workflows and build, test, and deploy their applications with ease. One common use case is to securely pass environment variables, such as API keys or passwords, to a Go program during the workflow execution in GitHub Actions. In this blog, we’ll walk through the process of setting up repository secrets, creating a GitHub Actions workflow, and using those secrets as environment variables in a Go program.
Creating Secrets in GitHub Repository:
- Open your GitHub repository on the web.
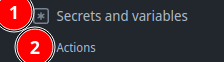
- Navigate to “Settings” in the right sidebar.
- Click on “Secrets and variables” in the left sidebar and then “Actions”.
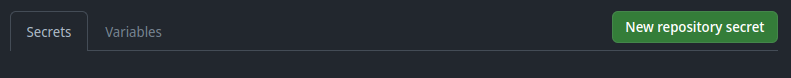
- Click on “New repository secret.”
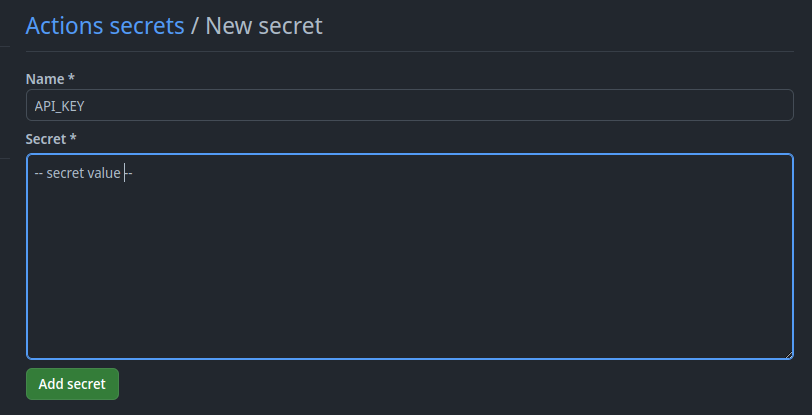
- Enter the name of the secret (e.g., API_KEY) in the “Name” field.
- Add the value of the secret (e.g., your actual API key) in the “Value” field.
- Click “Add secret” to save it.
Repeat the process for any other sensitive information you need to store, like passwords or access tokens.
Creating the Go Program:
For this example, let’s assume we have a simple Go program that requires two sensitive environment variables, API_KEY and DB_PASSWORD. Create a new file named main.go in the root of your repository with the following content:
package main
import (
"fmt"
"os"
)
func main() {
apiKey := os.Args[1]
dbPassword := os.Args[2]
fmt.Println("API_KEY:", apiKey)
fmt.Println("DB_PASSWORD:", dbPassword)
// Your main program logic here...
}
Creating the GitHub Actions Workflow:
- In the root of your repository, create a new directory named
.githubif it doesn’t exist. - Inside the
.githubdirectory, create another directory namedworkflows. - Create a new file named
main.ymlinside theworkflowsdirectory with the following content:
name: Execute Go Program
on:
push:
branches:
- main
jobs:
execute_go_program:
runs-on: ubuntu-latest
steps:
- name: Check out repository
uses: actions/checkout@v3
with:
persist-credentials: false
- name: Set up environment and run Go program
env:
API_KEY: ${{ secrets.API_KEY }}
DB_PASSWORD: ${{ secrets.DB_PASSWORD }}
run: go run main.go "${{ env.API_KEY }}" "${{ env.DB_PASSWORD }}"
Explanation of the Workflow:
- The workflow will run on every push event to the
mainbranch (on: push: branches: [ "main" ]). - It defines a single job named
execute_go_program. - The job runs on the latest version of the Ubuntu operating system (
runs-on: ubuntu-latest). - The first step checks out the repository (
uses: actions/checkout@v3). - The second step sets up the environment variables
API_KEYandDB_PASSWORDusing repository secrets (secrets.API_KEYandsecrets.DB_PASSWORD). - The third step runs the Go program using
go run main.goand passes the environment variables as command-line arguments ("${{ env.API_KEY }}"and"${{ env.DB_PASSWORD }}").
Conclusion:
By following the steps above, you can securely pass environment variables to your Go program in GitHub Actions. The use of repository secrets ensures that sensitive information is kept private and not exposed in plaintext in your workflows. With this setup, you can confidently automate your Go programs with GitHub Actions while maintaining a high level of security for your sensitive data.
FAQs:
-
Q: Can I use other programming languages with GitHub Actions?
- Yes, GitHub Actions supports multiple programming languages and environments.
-
Q: Is there a limit to the number of secrets I can store in my GitHub repository?
- GitHub allows you to store up to 100 secrets per repository.
-
Q: Can I access the secrets programmatically from my Go program?
- Yes, as shown in the example, you can access secrets using environment variables in your Go program.
-
Q: How can I ensure that only authorized users can access the repository secrets?
- GitHub provides access controls and permissions to manage who can view and use repository secrets.
-
Q: Are repository secrets encrypted at rest?
- Yes, GitHub encrypts and securely stores repository secrets to ensure their protection.