Leviathan Level 0 to Level 1 | Basic Exploitation Techniques
Learn linux command by playing Leviathan wargame from OverTheWire. This wargame doesn’t require any knowledge about programming - just a bit of common sense and some knowledge about basic *nix commands.
Below is the solution of Level 0 → Level 1 and Level 1 → Level 2. In this post we will learn how to use a debugging tool ltrace to exploit a program.
Level 0
To login to the first level use:
Username: leviathan0
Password: leviathan0
The command to login into level 0 is ssh leviathan0@leviathan.labs.overthewire.org -p 2223
and the password is leviathan0 .
Leviathan Level 0 → Level 1
It is given at the homepage of this wargame that data for the levels can be found in the homedirectories. You can look at /etc/leviathan_pass for the various level passwords.
In leviathan0 directory there is a directory .backup whose user is leviathan1. This can be found by command ls -la.
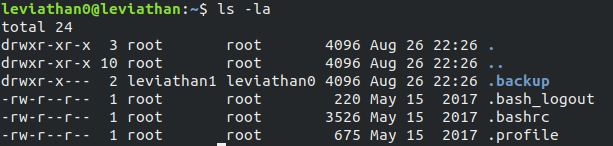
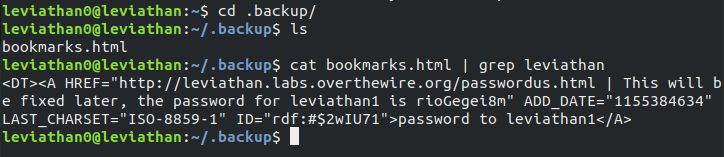
In .backup directory there is a file bookmarks.html. This file may contain the password for next level. To find that, the command is cat bookmarks.html | grep leviathan and the password is rioGegei8m.
Leviathan Level 1 → Level 2
Command to login is ssh leviathan1@leviathan.labs.overthewire.org -p 2223 and password is rioGegei8m .
We have an executable file check with setuid for user leviathan2 and it can be executed by leviathan1.
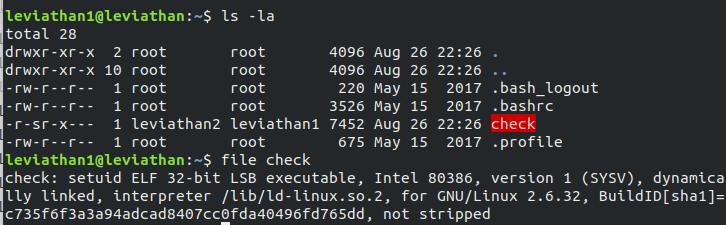
But when we execute it, it asks for the password.
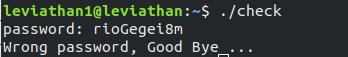
To find the password, which is asked after executing binary file, we will use ltrace command.
ltrace is a diagnostic and debugging tool for the command line. It intercepts and records the dynamic library calls which are called by the executed process and the signals which are received by that process. It can also intercept and print the system calls executed by the program.
This command will tell about all the system call this binary file made when it is executed.
The command is
1
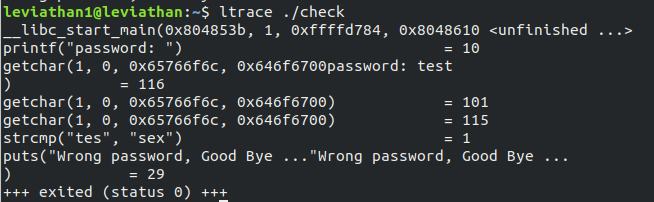
ltrace ./check
and we are prompted to enter password. We enter test and one of the function called is strcmp. It compares test with sex. This means sex is the password the binary file need.
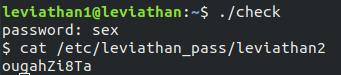
After we enter sex as password, we are in root shell and then we can see the password for next level using command cat /etc/leviathan_pass/leviathan2 and the password is ougahZi8Ta .
Reference : Chapter 9. ltrace
LTRACE(1)
Next Posts
Leviathan Level 2 → Level 3
Leviathan Level 3 to Level 4
Leviathan Level 5 to Level 6
Other Wargames
Bandit Wargame from OverTheWire All Level Solutions
Krypton Wargame from OverTheWire All Level Solutions